Because Recovery Isn’t Enough Anymore
There’s a growing realization in enterprise IT: it’s no longer enough to simply have recovery mechanisms in place; you must ensure that the recovery data itself remains untouched. As ransomware, rogue scripts, and even human error continue to compromise data protection strategies, one weak link keeps surfacing: the ability to tamper with recovery points.
With the upcoming DataCore SANsymphony 10.0 PSP21 release, Immutable Snapshots close that gap. They give organizations a way to lock recovery data at the source, ensuring that once a snapshot is captured, it cannot be modified, deleted, or reconfigured until its defined retention period expires. Even administrators can’t override it.
This is more than another checkbox in the data protection stack. It marks a fundamental shift in how SANsymphony safeguards data integrity, delivering confidence that your last known good copy will always stay that way.
A Line That Can’t Be Crossed
Every recovery strategy depends on one assumption that when the moment comes, your data will be exactly as it was. Yet most recovery points remain vulnerable, subject to human error, automation missteps, or deliberate compromise by cyberattacks.
Immutability restores that certainty. It defines a boundary where data stops being transient and becomes permanent: a record that endures exactly as it was created. Once data crosses that line, it becomes a verifiable, read-only image of truth. By removing the possibility of alteration, immutable snapshots bring permanence to protection, turning storage into a source of assurance rather than uncertainty — a foundation of true cyber resilience.
When Protection Becomes Proof
In today’s environment, the question is no longer “Do you have a copy?” It’s “Can you prove it’s still real?”
Immutable snapshots don’t just preserve data; they preserve trust. They mark a point in time that cannot be negotiated, rewritten, or quietly adjusted to fit a narrative. What was true then stays true now, verifiable down to every block.
For organizations navigating audits, regulations, or recovery events, that assurance is transformative. It turns backup from an act of caution into an instrument of confidence. And with SANsymphony embedding this integrity at the storage layer itself, immutability becomes something far stronger than protection — it becomes proof that your data is exactly what it claims to be.
Immutability Engineered into the Storage Foundation
In SANsymphony, immutability isn’t a wrapper or an add-on; it is built directly into the storage fabric. Every immutable snapshot enforces protection at the lowest level, independent of user actions or administrative intent. Once sealed, its state is final until the defined retention period expires.
That enforcement is absolute. No command, privilege, or process can alter or delete an immutable snapshot before its time. Even during maintenance windows, reboots, or failovers, recovery points remain locked and verifiable.
Behind that certainty is deliberate engineering:
- Retention enforcement that cannot be shortened below 24 hours, preventing premature unlocks or accidental deletions.
- Hash-based integrity verification to validate each immutable snapshot against its cryptographic seal and prove it hasn’t changed.
- Seamless management through the management console, PowerShell, or REST API, offering operational control without weakening protection.
- Persistence across all conditions even after crashes or restarts, immutable snapshots are restored in read-only mode, ensuring continuous protection.
This is protection expressed as architecture: immutability that exists by design, not by configuration. It transforms the storage layer into a final, incorruptible line of defense for enterprise data.
Working with Immutable Snapshots
Creating an Immutable Snapshot
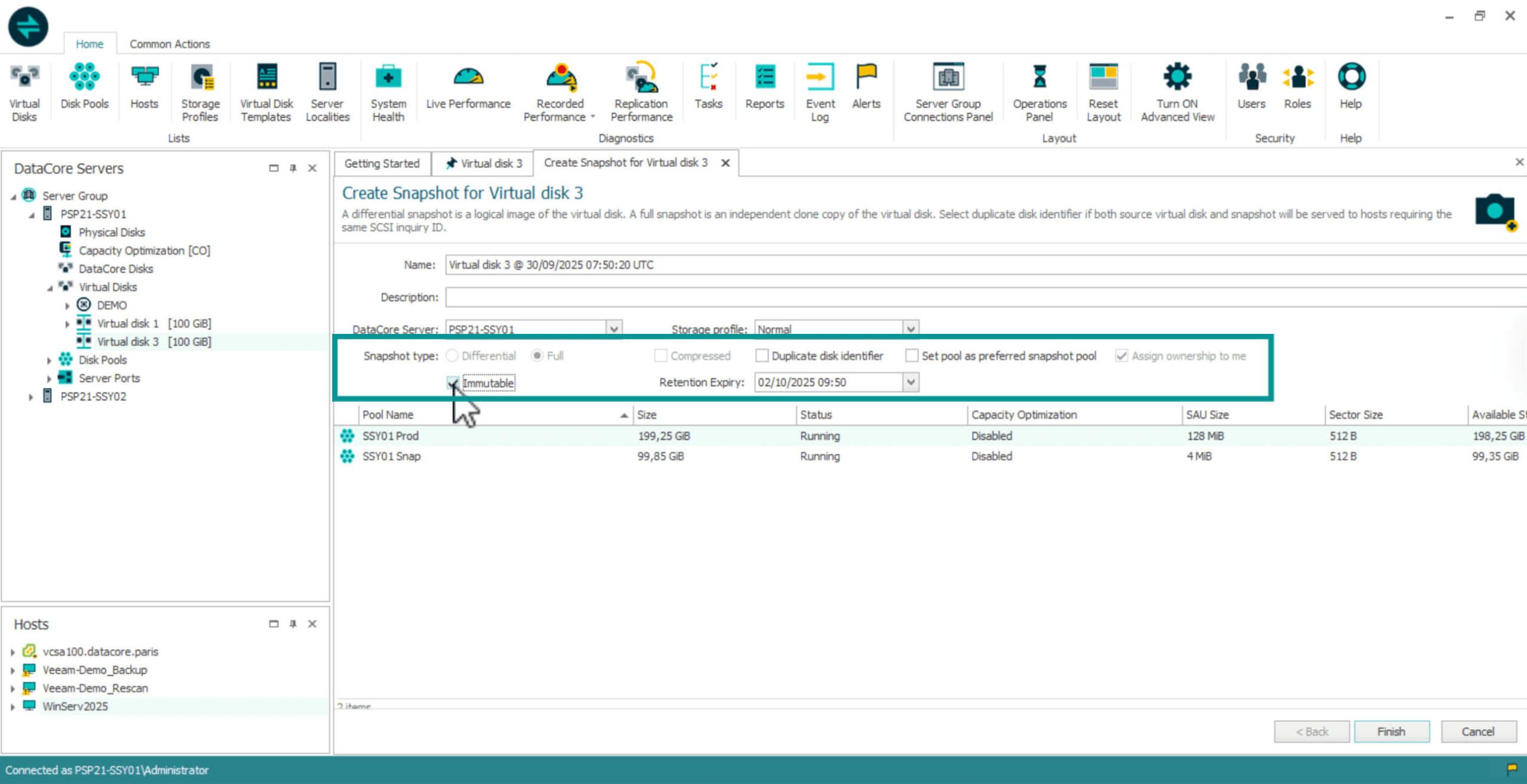
Creating an Immutable Snapshot in SANsymphony begins like any standard snapshot operation: from the Virtual Disk Details page, select Create Snapshot. When you enable the Immutable checkbox, SANsymphony automatically converts the snapshot type to Full, since immutability requires a complete, independent image of the source.
Once immutability is selected, SANsymphony enforces a minimum retention period of 24 hours. If a shorter duration is entered, the system automatically adjusts it and alerts you before proceeding.
During creation, hash calculation starts automatically. Every data block in the snapshot is included in the cryptographic hash, forming a verifiable seal of integrity. Progress is displayed as a percentage in the Immutability tab. Even while hashing is in progress, the snapshot is already read-only and protected from change.
When hashing completes successfully, the snapshot transitions to the Retention Locked state. From this point until the retention period expires, no command, privilege, or process can alter or delete it — not even an administrator.
Making an Existing Snapshot Immutable
Immutability can also be applied to snapshots that already exist. From the Immutability tab of a selected snapshot, choose Make Immutable, then set the retention expiry. Once confirmed, the same rules apply: hashing begins automatically, the snapshot becomes read-only, and status changes to Retention Locked after completion.
This capability allows administrators to strengthen protection retrospectively. For example, securing a critical snapshot after validation testing or before archival retention.
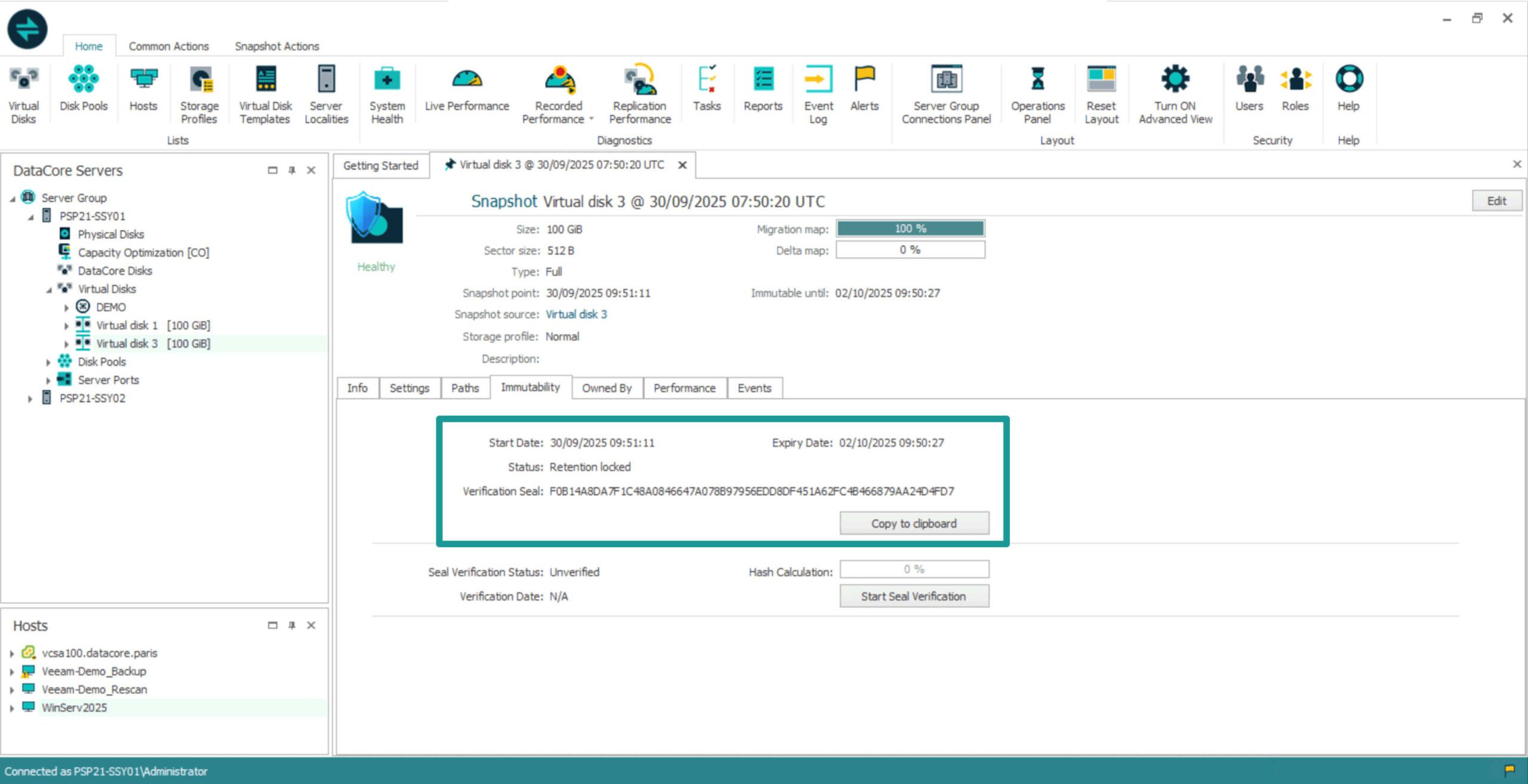
Verifying Integrity
At any point, you can run Seal Verification to confirm that a snapshot’s hash still matches its stored seal. If the values match, the snapshot status updates to Verified. If discrepancies are detected, the snapshot is flagged as Compromised, but it remains immutable and protected.
Seal verification ensures long-term trust, especially for organizations that must demonstrate chain-of-custody integrity or compliance with strict data retention regulations.
Enabling Compression
When creating snapshots — immutable or otherwise — you can optionally enable Compression, provided the selected pool supports capacity optimization. Compression reduces the storage footprint while maintaining the snapshot’s full immutability characteristics. For immutable snapshots, compression is applied at creation and preserved for the duration of the retention period, optimizing storage efficiency without altering data integrity.
Monitoring and Persistence
Immutable Snapshots are integrated with System Health monitoring. The console automatically raises warnings as snapshots approach expiry (by default, within three days). Administrators can view creation times, expiry dates, and hash-verification status in a single pane. Even after restarts, maintenance windows, or failovers, immutable snapshots are restored in read-only mode automatically. No manual reapplication or policy refresh is required — immutability persists by design.
Locked. Proven. Unbreakable.
Immutable snapshots mark a turning point in how organizations think about data protection. By embedding immutability directly into the SANsymphony architecture, they eliminate the last point of weakness — the ability to alter what should never change. Each snapshot becomes an unassailable record of truth, immune to tampering and time. In a landscape where recovery alone is no longer enough, this is the foundation of real resilience: data that doesn’t just survive but stays provably authentic, no matter what comes next.
Request a free trial of SANsymphony to test immutable snapshots in action.